RSECURITY
Dispelling Myths and Understanding
Download the Fact Sheet (PDF – 175kb)
04/07/2022 Draft Guidance: Cybersecurity in Medical Devices: Quality System Considerations and Content of Premarket Submissions
This draft guidance replaces the 2018 draft version, which emphasizes the importance of understanding that all medical devices are designed securely, enabling new cybersecurity risks to be mitigated throughout the Total Product Life Cycle, and it elaborates the outline of the FDA’s recommendations more clearly for premarket submission to address cybersecurity concerns.
03/08/2022 Cybersecurity Alert: Vulnerabilities identified in medical device software components: PTC Axeda agent and Axeda Desktop Server
Ready to Streamline Your Regulatory Compliance?
Join hundreds of companies who trust OMC Medical for their regulatory needs. Get expert guidance and ensure compliance across all markets.
Call Now +44 208 066 7260The PTC Axeda agent and Axeda Desktop Server are cloud-based technologies that allow people to securely view and operate the same desktop through the Internet. The Axeda agent and its desktop server are owned by the computer software company PTC.
The FDA alerts all medical device users and manufacturers about a cybersecurity vulnerability identified for the Axeda agent and Axeda Desktop Server.
The agent and desktop server of Axeda are used in many medical devices across several medical device manufacturers, and all the versions of the Axeda agent and Axeda Desktop Server are affected.
On the 8th of March, 2022, the Cybersecurity and Infrastructure Security Agency (CISA) published an advisory, ICSA-22-067-01, on these vulnerabilities.
Any successful exploitation of this vulnerability could allow an unauthorized attacker to take complete control of the host operating system, resulting in full system access, remote code execution, reading or changing the configuration, system file access, accessing log information, and other denial condition.
These vulnerabilities may result in changes to the functions of the medical device and impact the availability of the remote support functionality.
As a result, PTC recommends that affected manufacturers:
- To upgrade Axeda agent Version 6.9.2 build 1049 or 6.9.3 build 1051 while running older versions of the Axeda agent.
- Also, to configure the Axeda agent and Axeda Desktop Server to listen only on the local host interface 127.0.0.1.
- Then, Provide a unique password in the AxedaDesktop.ini file for each and every unit.
- Remove the installation file.
- Make sure to delete the ERemoteServer file from the host device.
- Never use ERemoteServer in production.
- When running the Windows operating system, first configure Localhost communications (127.0.0.1) between ERemoteServer and Axeda Builder.
- When running in Windows or Linux, only allow connections to ERemoteServer from trusted hosts and block all others.
- Configure the Axeda agent for the authentication information required to log in to the Axeda Deployment Utility.
So, Cybersecurity is one of the crucial aspects of today’s fast pacing digital world. The threats caused by Cybersecurity, especially on medical devices, are hard to deny. It is important to learn how to defend themselves from them and create a safe environment for the usage of medical devices.
EU MDR and IVDR
In the EU, both the MDR and IVDR Annex I create requirements for mandate consideration of medical device cybersecurity, and the Medical Device Coordination Group (MDCG), in its guidance, explains to the manufacturers of medical devices how to fulfil all the relevant essential requirements regarding Cybersecurity.
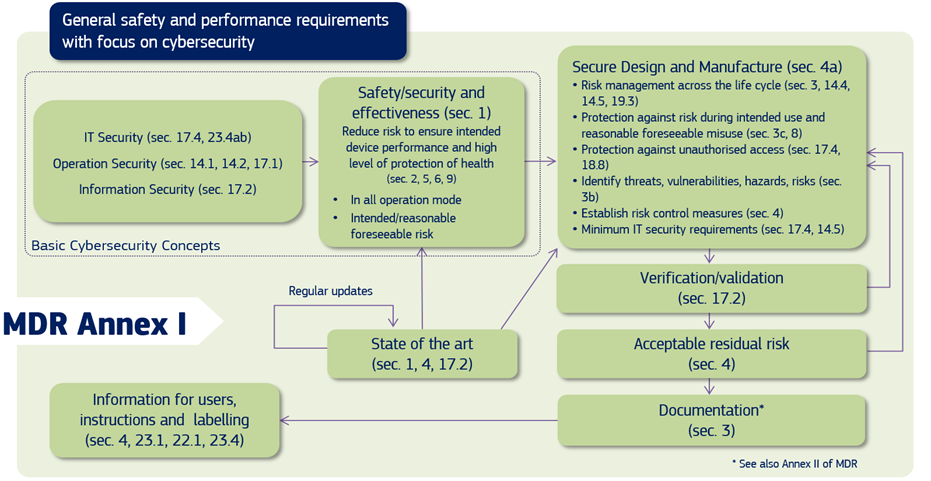
Figure 1: Cybersecurity requirements contained in MDR Annex I
The NIS Directive also provides for legal measures to increase the overall level of Cybersecurity in the EU.
GDPR (General Data Protection Regulation) helps the manufacturers of medical devices in regulating, protecting and processing personal data by the individual, company or organization that relates to the EU.
The EU Cybersecurity Act certifies Cybersecurity for ICT products, services, and processes.
According to the Cybersecurity Act, manufacturers are required to demonstrate state of art in the design, development, and improvement of their medical devices throughout their life cycle.
During that period, the manufacturers must consider the safety, security, and efficacy of the medical devices, and in vitro diagnostic safety mechanism design must be considered early during the manufacturing process.
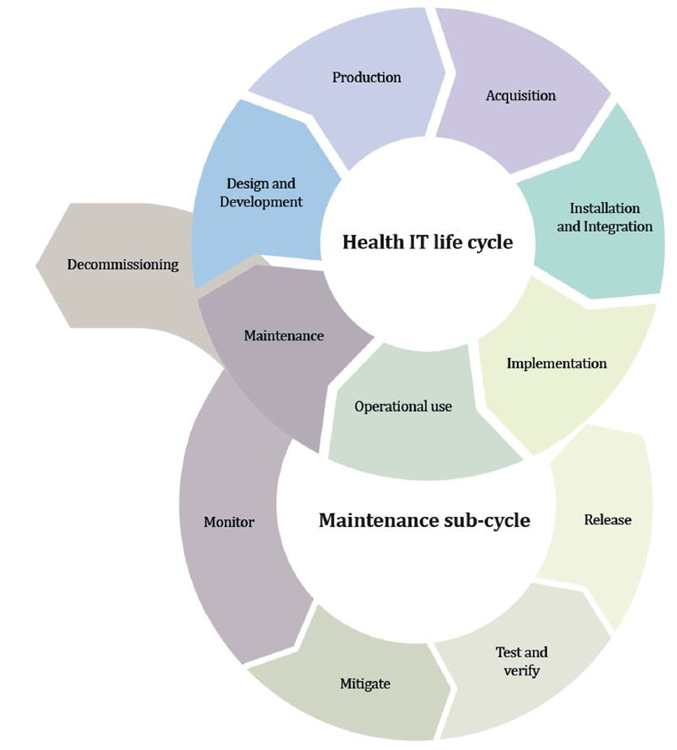
Figure 4: Lifecycle stages
The MDCG has proposed some key philosophies of the staged security concept strategy (“defense in depth strategy”) as follows:
- Security management
- Specification of security requirements
- Security by design
- Secure implementation
- Management of security-related issues
- Security update management
- Security risk management
The list of possible IT security requirements for the operating environment according to MDCG:
- Compliance with national and EU regulations (e.g., GDPR).
- Ensuring appropriate security controls are in place
- Ensuring the physical security of the medical device through security measures
- Ensure control and security of network traffic through proper measures
- Life Cycle Aspects
- Security measures specific to their workstations connected to the medical device.
- Security vulnerabilities related to the device hardware/software and third-party hardware/software used with the medical device.
- During the life of the devices, the manufacturer should implement the process to collect post-market information about the security of the device.
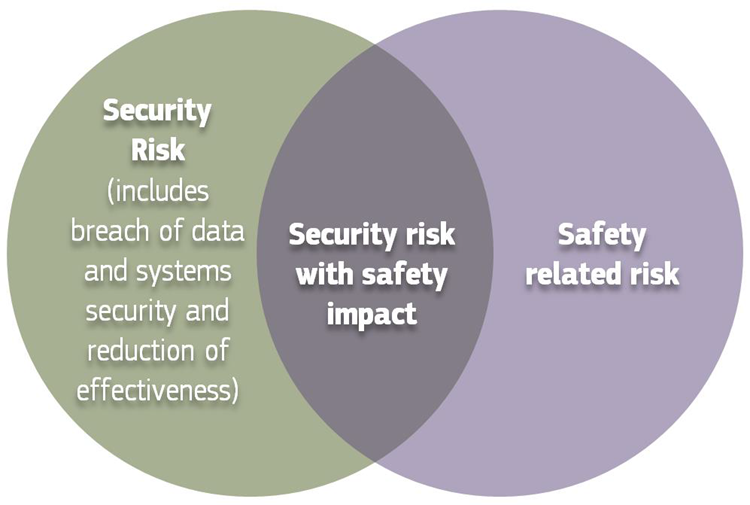
Figure 3: Cybersecurity measures may cause safety impacts
Based on the EU Cybersecurity Act, the manufacturer must provide the following information to the user of the medical device:
Specifications of the operating system
- IT security risk assessment information.
- Provisions for ensuring the integrity of software updates and security patches
- Product installation
- Security configuration options
- Initial configuration guidelines
- Step-by-step instructions for deploying security updates
- Description of the backup and restore functions for data and configuration settings
- Procedures for using all the medical devices in failsafe mode
The manufacturers are required to establish a post-market surveillance (PMS) system and actively keep these PMSs (Post Market Surveillance) up to date. Medical device cybersecurity requirements should be part of this PMS system.
Depending on the class of medical device, a PMS report or PSUR report will be generated, which concludes the analysis of all data from the market.